
secida im April
Wie immer mit interessanten Aktivitäten im April, dem Link zum Livestream und vielem mehr.

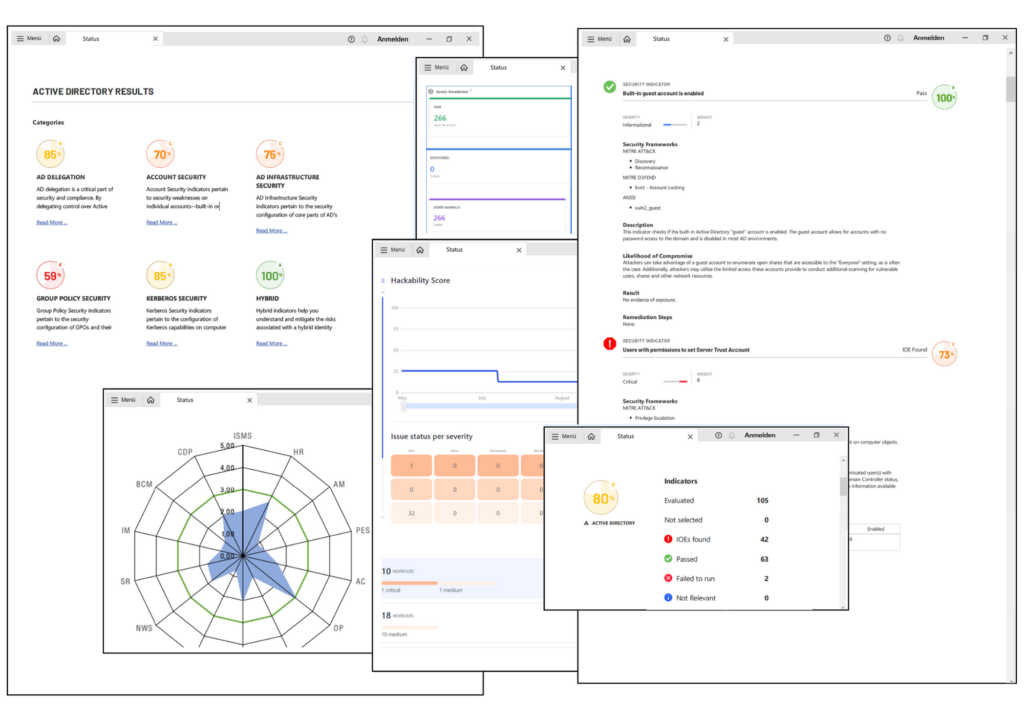
Die ganzheitliche Analyse der Cybersicherheit aus Managementsicht.

Im Rahmen von Transformations- und Carve-out-Projekten implementiert die secida AG zukunftsfähige, sichere IT-Komplettlösungen auf Basis von Microsoft-Cloud-Technologie. Mit unserem Fachwissen zu IAM, PAM und Directory Services steuern wir wesentliche Bestandteile von modernen Zero-Trust-Architekturen bei.

We support our clients from IT-carve-out to Microsoft 365 implementations

Integration of modern, cloud-based solutions into existing local data centers or implementation of cloud-only services
From A for Active Directory to Z for Zero Trust
We support our clients from IT-carve-out to Microsoft 365 implementations
Integration of modern, cloud-based solutions into existing local data centers or implementation of cloud-only services
From A for Active Directory to Z for Zero Trust


IT transformation
Die IT-Infrastruktur des Unternehmens ist dezentral aufgesetzt; die IT von zugekauften Unternehmen wurden nicht konsolidiert. Benutzeridentitäten werden in lokalen Verzeichnisdiensten verwaltet. Das Unternehmen plant neue Services in einer gemeinsamen Public Cloud-Umgebung aufzubauen, die weltweit von allen Mitarbeitern genutzt werden soll.

Cost optimization
The IT infrastructure for the company's web applications has developed over time. Different architectural concepts were used to provide application access (e.g. reverse proxy, federation). Licensing costs have escalated and the implemented solutions have partially overlapping functions.
As a consultancy secida is vendor-agnostic. We support our clients in selecting the optimal solution to their specific situation. To facilitate purchasing the products for our clientes when necessary, we have made the strategic decision to act as reseller ourselves.
In addition, we are a corporate member of the following networks:

We have a great story to tell:
Who we are, where we come from and where we want to go.
Contact Lisa for an initial conversation to learn more about each other.

Wie immer mit interessanten Aktivitäten im April, dem Link zum Livestream und vielem mehr.

Wie immer mit interessanten Aktivitäten im März, dem Link zum Livestream und vielem mehr.


Alpha Barry began his career in the Business Technology Office of McKinsey & Company, where he spent 7 years advising large companies on technology and IT issues. Subsequently, he worked in the top management of several successful startups in the software and consulting environment.
Alpha Barry joined the thyssenkrupp Group in 2012. Reporting directly to the Group CIO, he led programs to reorganize and integrate Group IT and IT infrastructure, and set up an in-house IT consultancy with 30 employees.
In 2016, Alpha Barry took over responsibility for the Group's cybersecurity during a critical cyberattack by professional perpetrators from the Far East. Since successfully defending against the attack, he has worked to secure the Group-wide IT infrastructure through modern Identity & Access Management, Privileged Access Management and Hybrid Cloud Security.
We founded secida to make digital identity and cloud-based IT infrastructure more secure across companies.

Benedikt Dietrich has been working on complex IT infrastructure and software architectures since 1998. Since 2000, he has been working as an IT entrepreneur and head of development departments with up to 150 employees.
Benedikt Dietrich has held the CTO role in several start-up companies and successfully developed market-leading solutions. With blue-zone AG, he built a technology leader in the cloud environment and was Microsoft Partner of the year in 2015.
From 2017 to 2019, Benedikt Dietrich successfully managed IAM and cloud projects in large industrial companies as a technical project manager, for example the redesign of a secure hybrid infrastructure for tens of thousands of users, or the successful migration of over 30,000 users to the O365 cloud.
At secida, Benedikt Dietrich uses his vast experience in dealing with modern cloud and security technologies to design and implement efficient and effective security systems for our customers.

Viktor Biletzki looks back on 25 years of experience in managing group-wide programs and projects. In the early 1990s, for example, he already worked as an IT project manager and consultant for the German Bundestag, later headed the Project Management Competence Center for the Mobility division at Nokia, or was responsible for carve-outs and integration as global program manager at Nokia Siemens Networks.
In 2014, he took over the responsibility for the successful realization of customer projects at Atos. In this role, he managed a wide variety of complex and critical projects, sometimes with a direct reporting line to top management.
In 2017, Viktor Biletzki joined thyssenkrupp Digital Projects as IT Project Director, where he, among other things, designed and implemented the central identity management service across the Group, realized an O365 migration, and introduced sustainable protection mechanisms as part of the cyberattack on the Group.
Viktor Biletzki left thyssenkrupp to successfully implement projects with secida AG in the areas of cybersecurity, cloud technologies and carve-outs at other companies.
The company's IT infrastructure is set up in a decentralized manner; the IT of purchased companies has usually not been consolidated. User identities are managed in local directory services. The company now wants to build new services in a shared environment in the public cloud, to be used by all employees worldwide. Ideally, old and new services should be used with a uniform user identity after a single login (single sign-on).
Lösung:
This enabled the onboarding of over 35,000 existing users in less than 6 months. It also enabled single sign-on for all services used by the user, whether in the data center or in the cloud. Today, mobile users can access efficient, automated support worldwide.
The IT infrastructure for the company's web applications has developed over time. Different architectural concepts were used to provide application access (e.g. reverse proxy, federation). Licensing costs have escalated and the implemented solutions have partially overlapping functions.
Lösung:
Savings of 25% of previous licensing and maintenance costs in the millions while maintaining security and functionality. Further cost reduction potential in operation due to decreasing complexity.
Professional hackers compromised administrative accounts and secured extensive access rights to data and servers. After successful mitigation of the cyber incident, the corporation wants to minimize the risk of future cyberattacks.
Lösung:
As a result, in addition to a significant increase in security, cost-saving effects were also achieved through consolidation. Since the introduction of the new security systems, no similarly large cyber incident has been detected.